Executive Summary
Routine monitoring identified repeated outbound HTTPS connections originating from a Windows workstation between approximately 01:30 and 04:00 local time. The system was assigned to a non-technical user and expected to remain idle during overnight hours.
Baseline traffic analysis was conducted to establish expected behavior during normal business operations. After-hours captures were then compared against this baseline to determine whether the activity represented benign system behavior or automated execution.
Investigation scope included packet capture analysis, session timing review, and host-based artifact validation within a controlled lab environment.
Scope & Environment
- Baseline packet capture (normal user browsing behavior)
- After-hours packet capture (~30 minutes)
- TCP conversation statistics (86 distinct conversations)
- Task Scheduler artifact review (Windows endpoint)
- Manual timeline reconstruction documentation
Evidence Locker
Selected screenshots from the controlled lab environment used during investigation. All artifacts are purpose-built for academic simulation.
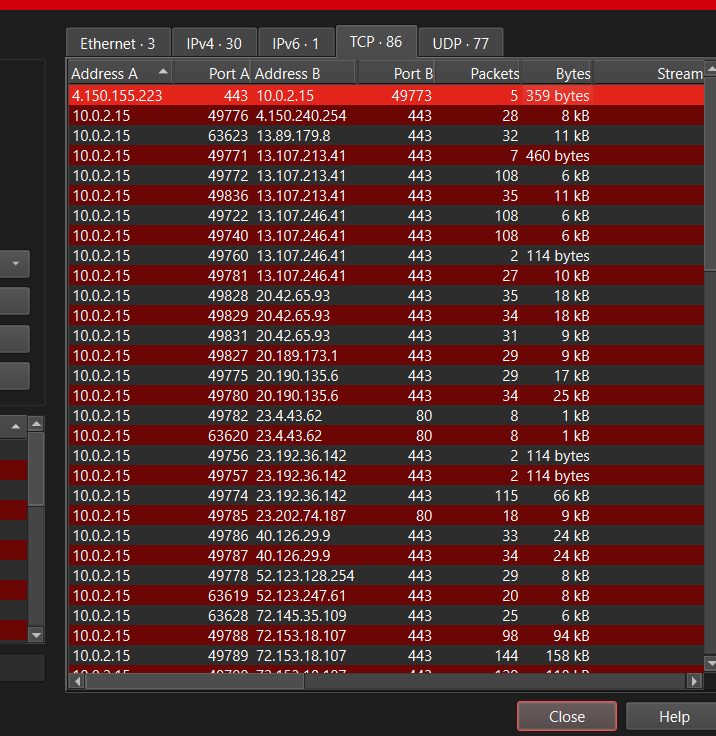
After-Hours TCP Conversations (86 sessions). Concentrated outbound HTTPS traffic to limited external destinations, inconsistent with baseline diversity.
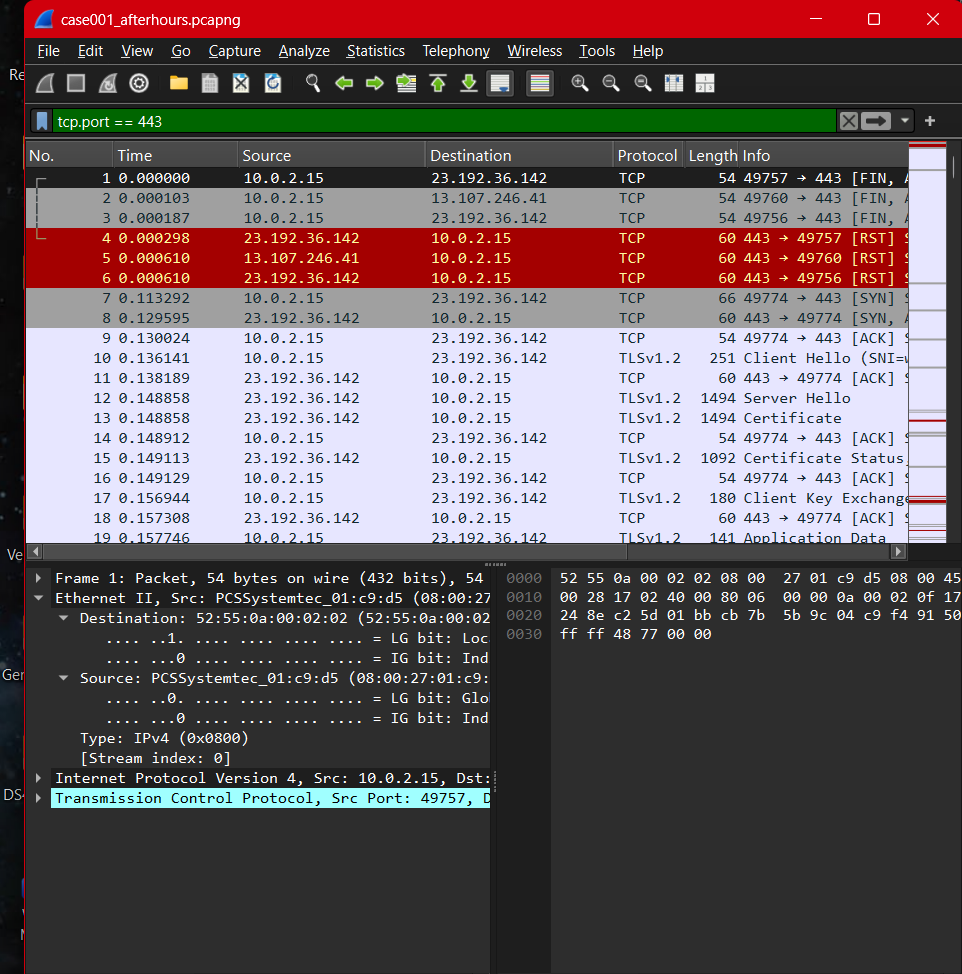
Packet-Level View (tcp.port == 443). Repeated TLS handshake and session establishment patterns suggest automated execution rather than user interaction.
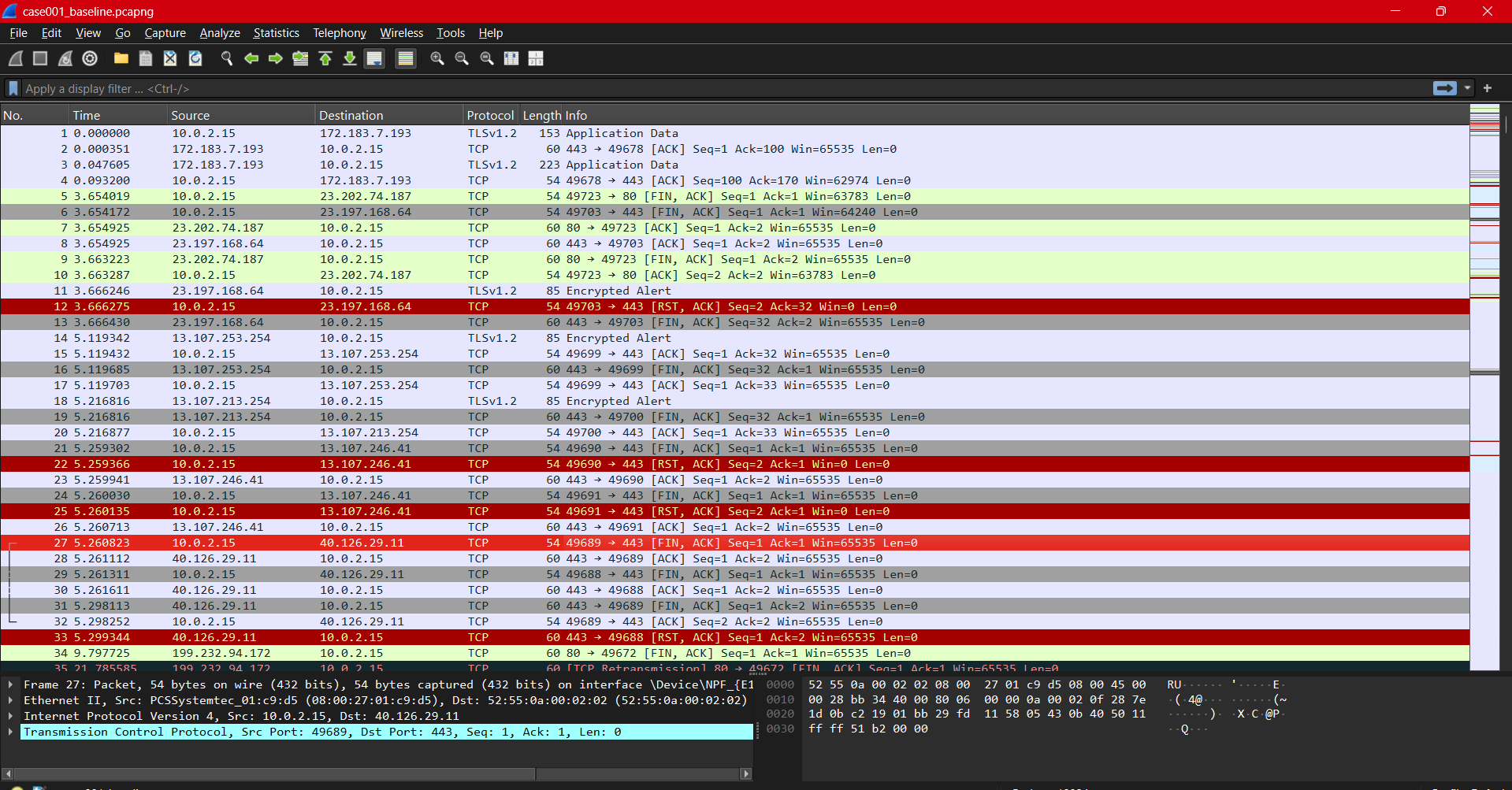
Baseline Traffic Capture. Normal browsing behavior shows irregular session timing and diverse destinations compared to after-hours activity.
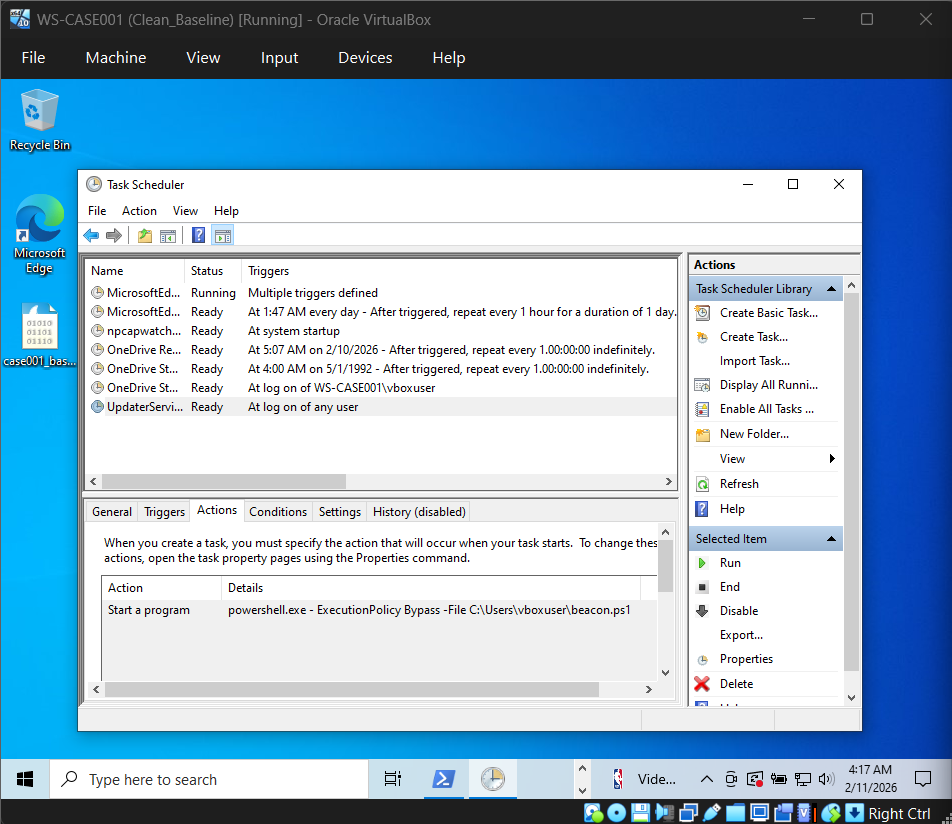
Scheduled Task Persistence (UpdaterService). Task configured to execute PowerShell script at logon, directly correlating to recurring after-hours network behavior.
Findings
During the after-hours capture window, the workstation (10.0.2.15) initiated repeated outbound HTTPS connections to a limited set of external IP addresses. Traffic exhibited consistent timing intervals, suggesting automated rather than interactive behavior.
Baseline traffic included normal HTTPS activity to diverse destinations; however, those connections were irregular, short-lived, and user-driven. The after-hours traffic demonstrated repetitive patterns not present in baseline data.
Endpoint analysis identified a scheduled task named UpdaterService configured to execute a PowerShell script at user logon. The script performed recurring outbound web requests at fixed intervals.
Correlation of network and endpoint artifacts supports the conclusion that the observed after-hours activity was automated and enabled by a persistent scheduled execution mechanism.
MITRE ATT&CK Mapping
- TA0003 — Persistence: Logon-triggered execution (Scheduled Task / script).
- TA0011 — Command and Control: Repeated outbound HTTPS sessions (behavioral).
Mapping is evidence-driven: each technique is tied to an observed artifact in the evidence locker and findings.
IOCs / Detection Notes
- Behavioral IOC: After-hours outbound TLS sessions clustered to limited destinations.
- Host IOC: Logon-triggered task invoking PowerShell with non-interactive flags.
- Detection idea: Alert when scheduled tasks trigger PowerShell + outbound TLS burst within X minutes.
Timeline
-
Event 1 — Persistence trigger configured
Scheduled task configured to execute a PowerShell script at logon. -
Event 2 — Trigger fires on logon
Logon event enables automated script execution without user interaction. -
Event 3 — Recurring after-hours outbound HTTPS
Repeated outbound HTTPS sessions observed during non-business hours. -
Correlation — Mechanism explains observed traffic
Persistence mechanism directly accounts for recurring network behavior.
Conclusion
The investigation identified automated outbound network activity inconsistent with baseline user behavior. A scheduled task persistence mechanism was validated as the execution vector responsible for the observed traffic. Conclusions are limited to evidence available within the lab environment, with no attribution or external threat classification made beyond supported artifacts.
Case Details
Skills Demonstrated
- • Packet-level traffic analysis
- • Baseline vs anomaly comparison
- • TCP conversation review
- • Scheduled task persistence identification
- • Timeline reconstruction
- • Evidence-based reporting